We are an experienced pentesting company based in Sweden with a vast range of expertise in the field of cybersecurity.
We Offer a Wide Selection of Services
Our professional and highly skilled team is dedicated to providing top-tier security solutions to protect your infrastructure, applications, and cloud environments from cyber threats.
Evaluate your Kubernetes security and identify vulnerabilities before they compromise your system.
Secure your cloud resources with comprehensive configuration and access control evaluation.
Identify and mitigate vulnerabilities in your network and systems from an external perspective.
Detect vulnerabilities within your internal network and protect against insider threats.
Test your defenses with real-world attack simulations and improve your security posture.
Protect your web applications from unauthorized access, data breaches, and cyber threats.
Meet the employees at Shelltrail
Research done by our employees
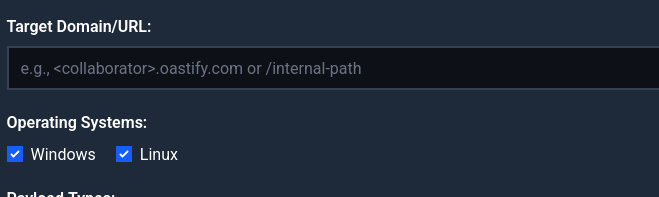
Web based payload generator for evaluating impact of SSRF vulnerabilities
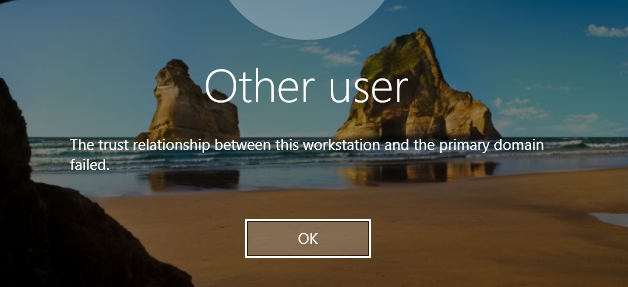
The post walks through the usage and the security considerations of domain join accounts used in Active Directory
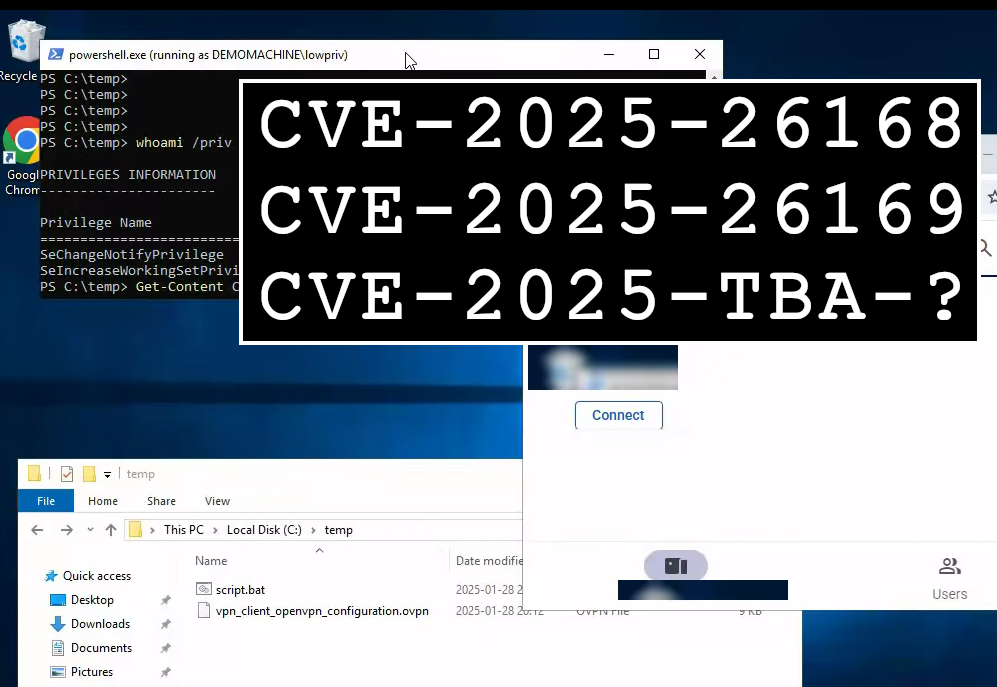
The post explains the process of finding and exploiting three vulnerabilities found in the IXON VPN client.
Connect with us